
How good are you at protecting your physical and digital data? What about company data? We’re seeing an increased number of security and vulnerability concerns at NW Computing, so we’ve compiled a few ‘how to’s” and helpful tips to better protect you and the company you work for.
(The following information can also be found in whole, or in part, on NW Computing Facebook and Instagram)
WHAT MAKES A GOOD PASSWORD?
 Is your online password ‘PASSWORD’? Does it contain your, or a relative’s, name, birthdate, favourite movie, place, game character, or any identifiable word for that matter? Well, your data, and the data of those people you’re acquainted with, is at risk. Here’s our recommendation:
Is your online password ‘PASSWORD’? Does it contain your, or a relative’s, name, birthdate, favourite movie, place, game character, or any identifiable word for that matter? Well, your data, and the data of those people you’re acquainted with, is at risk. Here’s our recommendation:
A strong password has a mix of upper and lower case letters, a special character (like @, $, !) and some numbers. It is also recommended to NOT USE consecutive numbers, birthdays, postcodes, and other significant dates or numbers. NW Computing recommends at least 8 random letters, characters and numbers.
Why does your company get you to change your login password(s) frequently? Although it can be annoying, most companies make it a policy for employees to change their passwords frequently. They put policies in place to prevent data breaches.
According to the Australian Cyber Security Centre:
“If your password or PIN is captured, guessed or stolen, a cyber criminal can potentially send emails from your accounts, withdraw money from your bank accounts, change files on your computer such as invoices, steal your identity. Weak passwords are easy for cybercriminals to guess. They use automated software that can potentially guess 350 billion passwords per second!”
WHAT IS 2-FACTOR AUTHENTICATION (2FA)?
When your company, IT department, and data provider are touting the benefits of 2FA (2-Factor Authentication) for protecting your data, it’s probably a good idea to initiate this added layer of security on all your online accounts.
 The 2-Step Verification process goes one step further than entering a password on a website by sending a code to your phone or device via text message (SMS). The user then enters that code when prompted by the site to get access.
The 2-Step Verification process goes one step further than entering a password on a website by sending a code to your phone or device via text message (SMS). The user then enters that code when prompted by the site to get access.
“Now that I have 2FA my data is safe, right?”
Not necessarily. Although your data is more secure with 2FA, hackers are relentless and will exploit security flaws in software, websites, and even a company’s cyber security.
Hackers have the potential to infiltrate a cellular/mobile network.
“2FA can fail when a hacker has hijacked a cellular network and can intercept text messages. They could then, for example, send a user a text message pretending to be from Google stating there’s a problem and they require the code about to be texted to them. The hacker then tries to login to the users Gmail account, prompting a 2FA text to the user. As the user has been told by ‘Google’ to expect this, they don’t think twice and reply with the code to the hacker, giving the hacker access to the user’s Gmail information.”
Now this scenario isn’t common, and 2FA is still much better than only entering a Username and Password on a website or App, but for an added layer of security NW Computing suggests an MFA (Multi-Factor Authentication) option. For every step forward by cyber security experts, hackers are right behind coming up with nefarious ways to steal your data.
MULTI-FACTOR AUTHENTICATION (MFA)
MFA is used via an Authenticator app on a mobile device. It protects your accounts from password theft and can be used in conjunction with 2-step verification (aka 2-factor verification or 2FA), which is offered on most of your social media and email accounts. In our recent Free Software Friday post on Facebook and Instagram we recommended Google Authenticator. It works on both Android and iOS devices. There are other apps for Multi-Factor Authentication, but Google Authenticator is the most accessible for most users.
Here’s how it works:
Although using 2-Step Verification (2FA) is good security practice, a “devoted hacker” can still get access to this code by going through your phone company.
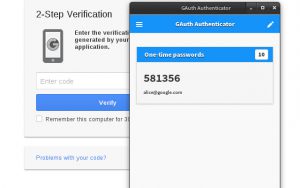 The Google Authenticator app provides an additional level of security by eliminating an SMS attack by using algorithms to generate six-digit codes on your mobile device (MFA – Multi-Factor Authentication).
The Google Authenticator app provides an additional level of security by eliminating an SMS attack by using algorithms to generate six-digit codes on your mobile device (MFA – Multi-Factor Authentication).
Now that it’s all set up, a website (a site you’ve authorised for this service) will prompt you for a code, which can be randomly generated through Google Authenticator app. This step bypasses the ‘text message’ that poses a potential risk.
CLEAN YOUR DESK!
 While it might seem like the company you work for is over-managing you, a Clean Desk Policy is important for security.
While it might seem like the company you work for is over-managing you, a Clean Desk Policy is important for security.
Keeping notes and paperwork on your desk, or in an unlocked draw, may seem convenient, but all it takes is one person getting access to the building, floor, or office you work in to steal sensitive information.
Never keep passwords on sticky notes, addresses on a notepads, or USB’s in unlocked draws. This data should be destroyed appropriately in a shredder or secure document bin.
It’s also good security practice to lock your computer when you leave your desk, even for a moment. It’s as easy as pressing (Windows key + L) on PC, or (Control + Command + Q) on a Mac. Many companies have their IT Partner set up auto lock on employees work computers, so they lock after a few moments of inactivity.
And if you’re sitting in an open office plan, with your computer monitor’s screen viewable by passersby, a privacy screen is an easy to install, and affordable, option to add that extra level of data security.
STRANGER DANGER. THE IMPORTANCE OF CLOSING THE DOOR BEHIND YOU.
Social Engineering is one of the business threats business face. “It’s the use of deception to manipulate individuals into voluntarily providing confidential or personal information that could be used for fraudulent purposes” (afta.com.au). This can be by SPAM or Phishing emails, a caller posing as a representative of a utility company or government agency, or as mentioned, someone who has hacked into a phone provider and requests your 2FA password. Social Engineering doesn’t necessarily need to compromise software or systems, it’s the “human interaction and persuasion” that makes this type of theft more difficult to deal with.
 Hackers use what’s called tailgating (or piggybacking) to gain access to a restricted areas of a building by using well intentioned employees who are overly courteous, and trusting of others who appear ‘official’ or ‘safe’. Have you ever held a secure door open for someone you didn’t know without seeing an ID or a security access card? Don’t blame yourself too much, most of us have done it at one time or another.
Hackers use what’s called tailgating (or piggybacking) to gain access to a restricted areas of a building by using well intentioned employees who are overly courteous, and trusting of others who appear ‘official’ or ‘safe’. Have you ever held a secure door open for someone you didn’t know without seeing an ID or a security access card? Don’t blame yourself too much, most of us have done it at one time or another.
The danger in being ‘courteous’ is it puts the company’s data at risk. A hacker posing as a technician, delivery driver, or even a fellow employee, will use your kind act to quickly make his, or her, way in and out of the office, along with all the data left on employee desks, mobile phones, laptops, and USBs. They also may have the opportunity to install malicious software on a computer, which will allow them to access the systems remotely.
It’s also never a good idea to let anyone, other than authorised company personnel, use your mobile phone or computer; even if they say “It will only be for a quick second”. That could be a one second you may regret.
UPDATE, DON’T PROCRASTINATE
 On 30 April, 2004 the Sasser Worm was released by 18 year old hacker Sven Jaschan. The virus affected Windows XP and 2000 OS’s, and exploited the LSASS (Local Security Authority Subsystem Service) which controls Windows security.
On 30 April, 2004 the Sasser Worm was released by 18 year old hacker Sven Jaschan. The virus affected Windows XP and 2000 OS’s, and exploited the LSASS (Local Security Authority Subsystem Service) which controls Windows security.
The most common issues were computers running at 100% usage, random crashes, and most commonly a countdown timer that appeared on screen, which eventually shutting down the user’s computer. In technical speak it is described as “exploiting a buffer overflow in the component known as LSASS…on the infected operating systems. The worm scans different ranges of IP
addresses and connects to victims’ computers mainly through TCP port 445.” – (tech monitor.ai)
The Sasser virus infected, and temporarily shutdown operations for Delta Airlines, Agence France-Presse (AFP) news agency, Goldman Sachs, a bank, hospital, coast guard and a university. IT providers and government agencies eventually found workarounds but not before causing millions in damage.
Microsoft actually caught this vulnerability prior to the virus, releasing a patch earlier that month. Users who updated their Operating Systems were safe, but hundreds of thousands were left vulnerable.
The lesson learned from the Sasser Worm is to always update your operating systems when prompted. Don’t procrastinate.
Your company’s IT department should have an update schedule in place and may even do it for you, alongside a policy for employees to shut down their computers at the end of the day allowing the updates to download to each PC.
ONLINE PRIVACY
 Want to keep your online browsing habits away from prying eyes? This eye opening CNET article shows you which settings on your preferred browser (Chrome, Firefox, Safari, Edge, Brave) to change to help protect your privacy. Or you can use DuckDuckGo which doesn’t track user searches.
Want to keep your online browsing habits away from prying eyes? This eye opening CNET article shows you which settings on your preferred browser (Chrome, Firefox, Safari, Edge, Brave) to change to help protect your privacy. Or you can use DuckDuckGo which doesn’t track user searches.
SCAMMERS LOVE TO PHISH

If you receive an unsolicited email or phone call asking for personal details, to click a link, or they offer you an incentive like a loan, it may be a scam.
Phishing is when the scammer tries to steal your personal information. They pretend to be a recognisable company (bank, internet provider, government agency…) and will ask you to update or confirm your details. They may even offer you a loan or product that’s too good to be true (guaranteed approval, very low interest rate, free iPhone…), or pressure you to “act now” before the offer runs out or the tax office/debtor takes legal action.
Never click a link or provide information to an unsolicited email or phone call. If you’re unsure of its legitimacy, tell them you’ll call them back using a number from the company’s website, or log into your account and confirm the link. Many companies have a message board on their website, linked to your account, that will match the information on your email; or call the company directly. The link could also be installing malware or malicious code onto your computer.
Other email and phone call “tells”:
- Spelling or grammar mistakes
- The sender’s email address doesn’t match the company (e.g. Gmail, Hotmail, Outlook…)
- Immediate payment requested
- The phone number is international or mobile
- Want to remotely access your computer
- Require payment in Bitcoin, gift cards, vouchers..
- Ask for your credit card, account, or bank card PIN
If you’ve been targeted by a scam, inform the company they were impersonating, ATO, call the police, and report it to ScamWatch to alert others.
HAVE A GOOD SECURITY CULTURE

Why do we wear Hawaiian shirts on Friday? Why do we do burrito birthdays? Why is everyone encouraged to contribute to the office music playlist? Because it’s the culture!
As written in an earlier blog post, culture is important because it shapes our identity, our communications and our behaviour when interacting with our clients and our peers. When it comes to Cyber Security – more often than not, all discussions will be about technical controls and mitigations of threats and ways to reduce risk through discrete systems. A positive security culture, and an aware workforce is an untapped and overlooked resource in protecting company assets (… more)
IN SUMMARY
– Choose a strong password
– Use 2-Factor Authentication
– Add even more online security by using Multi-Factor Authentication
– Clean your workspace
– Lock your computer
– Update your software
– Change your browser’s Privacy Settings
– Don’t provide confidential information over the phone or email.
– Don’t be so nice. Take part in your company’s security culture.
We’ll keep adding to this list of ‘How To’s’ and Tips. If you have any suggestions for cyber security content, or helpful tips of your own, send us a message on our Facebook or Instagram pages.
Need more help or advice? If you live in Australia or New Zealand, CONTACT US for a consultation. We provide multiple, effective, IT SOLUTIONS.
Have a nagging home or office IT issue? We may have the answer in one of our ASK AN NW IT EXPERT videos on our YouTube channel.
At NW Computing WE DO MORE.